xtrimi
🚧 SITE UNDER CONSTRUCTION 🚧
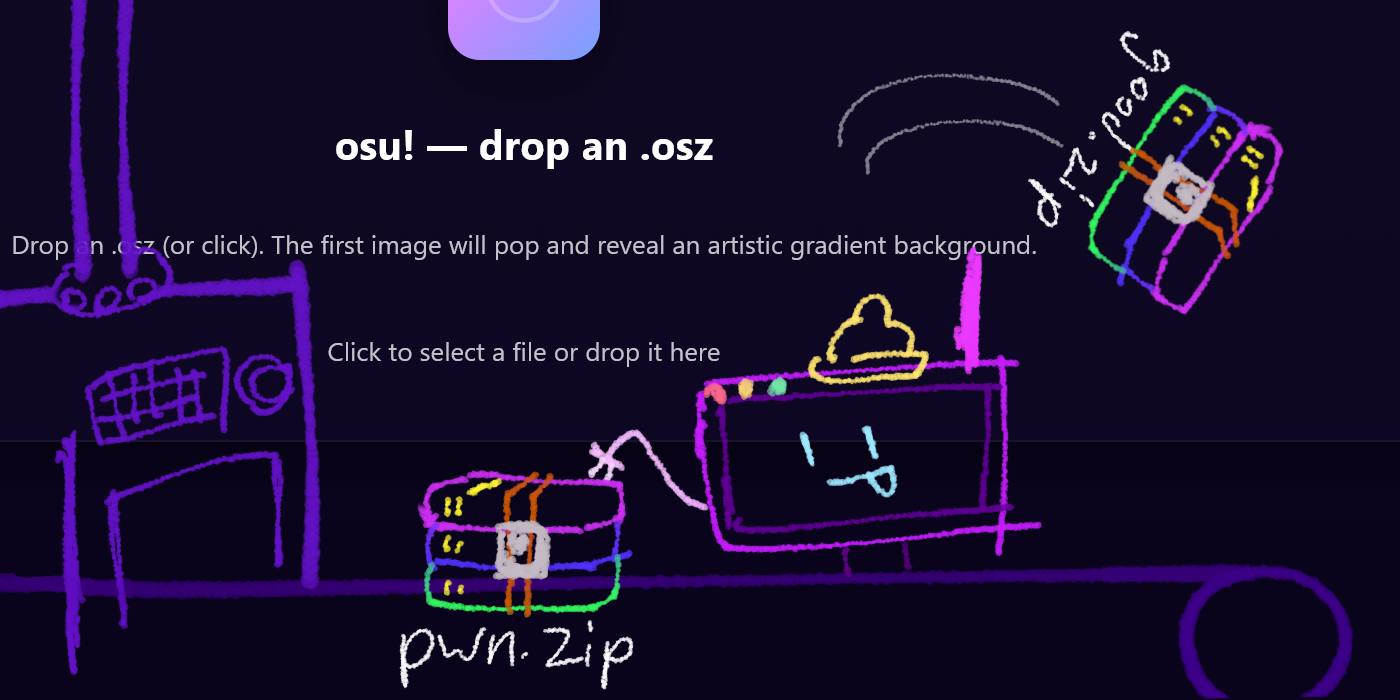
last weekend i played osu!gaming CTF 2025 with ICEDTEA, and managed to solve this fun challenge! i went down several rabbit holes (which my birdbrain thought was a dead end) and thought i’d share the process of how i solved it challenge we start with /index.html prompting us for an .osz, which sends it to /render and renders the map background alongside the gradient it sends back. there’s also two other endpoints, one being /upload: ...
played with NullCipher and got 23rd only solved baby challs cause i was busy lololol Interpol source: #!/usr/bin/env sage from Crypto.Util.number import * from flag import flag def randpos(n): if randint(0, 1): return True, [(-(1 + (19*n - 14) % len(flag)), ord(flag[(63 * n - 40) % len(flag)]))] else: return False, [(randint(0, 313), (-1) ** randint(0, 1) * Rational(str(getPrime(32)) + '/' + str(getPrime(32))))] c, n, DATA = 0, 0, [] while True: _b, _d = randpos(n) H = [d[0] for d in DATA] if _b: n += 1 DATA += _d else: if _d[0][0] in H: continue else: DATA += _d c += 1 if n >= len(flag): break A = [DATA[_][0] for _ in range(len(DATA))] poly = QQ['x'].lagrange_polynomial(DATA).dumps() f = open('output.raw', 'wb') f.write(poly) f.close() the randpos function stands out the most, so lets analyze it it basically flips a coin and does one of the following: ...
realized i suck so bad so i just gave up midway in and dropped out of top 5 lmfao Web Tomorin db 🐧 classic path traversal chall: func main() { http.Handle("/", http.FileServer(http.Dir("/app/Tomorin"))) http.HandleFunc("/flag", func(w http.ResponseWriter, r *http.Request) { http.Redirect(w, r, "https://youtu.be/lQuWN0biOBU?si=SijTXQCn9V3j4Rl6", http.StatusFound) }) http.ListenAndServe(":30000", nil) } this hacktricks section has our solution: In golang, the library net/http usually transforms the path to a canonical one before accessing it: /flag/ – Is responded with a redirect to /flag /../flag — Is responded with a redirect to /flag /flag/. – Is responded with a redirect to /flag However, when the CONNECT method is used this doesn’t happen. So, if you need to access some protected resource you can abuse this trick: curl --path-as-is -X CONNECT http://gofs.web.jctf.pro/../flag and thus we execute curl --path-as-is -X CONNECT http://chals1.ais3.org:30000/flag flag: AIS3{G01ang_H2v3_a_c0O1_way!!!_Us3ing_C0NN3ct_M3Th07_L0l@T0m0r1n_1s_cute_D0_yo7_L0ve_t0MoRIN?} ...
2nd again. god damnit. the Curse has unfortunately not been lifted WarmUp Welcome Start your CTF Challenge! THJCC{w3lc0m3_70_7hjcc} self-explanatory beep boop beep boop obligatory cipher spam chall binary -> b64 -> THJCC{n0rm4l_3nc0d1n6} Discord Challenge hate ai injection challs and think they should never be in ctfs in the first place? fret not! someone already wrote a payload for u: flag: THJCC{j01n_d15c0rd_53rv3r_f1r57} Web Headless I think robots are headless, but you are a real human, right? ...
we got 12th! yay prob wouldve gotten higher but the remaining chals are literally just mind reading and i cba ill only be explaining chals i care about & all web Web Grandma’s Secret Recipe we can login as 'kitchen helper' but we need to access the pantry as 'grandma' checking our cookies we have cookies checksum and role throwing checksum into a hash checker we know its md5, so we can just throw a md5 hash of ‘grandma’ and edit cookie to get through ...
ill wriet this in like 12 hours idk its now 1 month later masterful procrastination Prismatic Blogs overview we’re provided with two endpoints: /api/login/ and /api/posts/ the service uses prisma database and initialize 4 users with randomized password our flag is in one of the 4 users’ post, except it isn’t published we can’t really do much with /login/, so lets check /posts/: app.get( "/api/posts", async (req, res) => { try { let query = req.query; query.published = true; let posts = await prisma.post.findMany({where: query}); res.json({success: true, posts}) } catch (error) { res.json({ success: false, error }); } } ); notice that our query is directly passed into findMany without any sanitizations. can we exploit that? ...
dude i was doing ECTF prior to this and didnt see this ctf coming up literally hours after i was wondering why i dont see big names on ECTF leaderboard but after solving i realized the reason was chals were abysmally bad there i sacrificed a good(?) ctf for a garbage ctf ts pmo so anyways this became a “how many chals can i solo solve in 4 hours” challenge! (it was 9) just kidding i focused on web (some chals im too lazy to explain) ...
i hunted with Untitled CTF Game last weekend and ended up in 34th place, which was Kinda awesome i mained web but also sniped some easy challs, which i will be yapping abt in this post Forensics deldeldel [50] I managed to log more than just keys… perhaps it was too much data to capture? we’re given klogger.pcapng that consists of numerous USB packets given they’re keypresses from desc, i used this repo to parse the keypresses: ...
didn’t expect to get 2nd LOL Welcome Welcome 0x2 [100] we’re told to score 10k on the main page’s snake game: no way im doing that! let’s look for the source code f12, ctrl+u and right click is blocked, but we can use view-source:https://ctf.scint.org, then ctrl+f and there’s our flag! THJCC{Sn4ke_G4me_Mast3r} Discord 0x2 [100] run get_flag command using the bot… let’s use slash commands! mfw you can’t right click on bot messages to copy text flag: THJCC{🇩 🇮 🇸 🇨 ⭕ 🇷 🇩 🚀 🚀 🚀 💥 💥 } ...
ik this is like 1 month ago but i was busy with working on udg2 april fools so here we are this was the most solved chall but i spent an embarrasingly long time solving it guess i have a massive skill issue challenge we’re presented with a textbox input here, which will display a message on the page when it’s submitted, along with a button that shares our message with the admin bot the admin bot carries a flag cookie on its visit, so i figured i need to make the bot send the cookie to us somehow ...